Fortinet has an ongoing Security problem. Over a hundred CVEs were reported on vulnerabilities in Fortinet VPNs and other solutions during 2024 (See Ref 1), including critical ones like CVE-2024-55591 (Ref 2). In the first few weeks of 2025, we’ve seen two new CVEs reported for Fortinet solutions. Both get classed as High Risks on the CVE risk scale.
Secure remote access is crucial to many organizations. Even with an increased push for a return to the office, it’s undeniable that remote work and hybrid working are now a core part of information work. Securing these remote connections to on-premise systems and the cloud is vital. The increased attack surface presented by a dispersed workforce has not gone unnoticed by criminals.
Relying on legacy VPN solutions like Fortinet exposes organizations with remote workers to constant security risks. Fortinet’s record of vulnerabilities over the last few years highlights an urgent need for businesses to adopt security solutions that are better suited for the new world of work. It’s not feasible to keep patching VPNs to deal with new Fortinet vulnerabilities as they get discovered and reported, not to mention the possibility that there are zero-day vulnerabilities in Fortinet VPN solutions that bad actors exploit before a CVE and fix are published.
Organizations can proactively boost the security of their remote access networks by integrating Cloudbrink’s high-performance ZTNA that is included with their personal Secure Access Service Edge (SASE). Cloudbrink eliminates these vulnerabilities inherent in legacy VPN solutions, offering zero-trust, high-performance, and automated security capabilities that neutralize threats before they materialize.
This blog will highlight Fortinet’s recurring security vulnerabilities, the technical advantages of Cloudbrink’s architecture, and why businesses should integrate Cloudbrink as an essential layer in their remote access security stack.
The Persistent Security Risks of Fortinet VPN Solutions
I highlighted a few of the recent Fortinet CVEs in the introduction. However, I want to stress that dealing with these ongoing CVEs over time is untenable. There are 123 Fortinet CVEs with 2024 in their name and 2 with 2025 in their name this year so far (Ref 1).
Attackers actively exploited the critical CVE-2024-55591 in the wild during January 2025. This vulnerability allows remote attackers to gain super-administrative access to affected FortiOS and FortiProxy devices. The attack method uses a specially designed Node.js WebSocket request to exploit improper input validation, enabling attackers to gain full control over the Fortinet device. Multiple versions of FortiGate firewalls and FortiProxy are affected.
This critical vulnerability is not an isolated incident. Fortinet’s VPN products have suffered from multiple zero-day exploits. With each new CVE, businesses must scramble to patch their Fortinet systems, disrupting operations and introducing new attack vectors. Instead of engaging in this reactive cycle, organizations should adopt a solution that is inherently immune to such vulnerabilities. Cloudbrink provides such a solution for businesses looking to augment their existing Fortinet infrastructure or to deploy as a complete remote access security system.
Augmenting and Securing Your Fortinet VPNs
For businesses with significant investments in and who are currently relying on Fortinet but want immediate security improvements, you can deploy Cloudbrink as a protective cover of defence securing the existing infrastructure and giving time for a gradual migration without requiring a complete infrastructure overhaul. With Cloudbrink, you can:
- Immediately mitigate the recent CVEs in your VPN infrastructure
- Prevent exploitation of any similar future zero-day vulnerabilities
- Improve the remote access experience for your users
- Extend the useful life of your existing security investments
Cloudbrink’s Fast Edge nodes complement current Fortinet gateways, delivering an immediate security enhancement. Cloudbrink’s IPSec tunneling functionality maintains compatibility with existing enterprise firewalls and security protocols. This allows organizations to boost security today and slowly migrate from Fortinet VPNs to a more secure, efficient, and scalable solution — if that’s something they want to do.
Complete migration is not required to get the benefits of Cloudbrink running alongside existing Fortinet infrastructure. But remember, you should keep patching the ongoing CVEs for as long as you retain Fortinet infrastructure. The Cloudbrink layer means you won’t be worrying about Zero-day exploits being used to breach your organization.
The security challenges accompanying traditional VPN solutions like Fortinet aren’t going away – they’re intensifying. Continuing to expose your network through inbound VPN connections creates unnecessary risks that organizations can eliminate using Cloudbrink’s innovative approach.
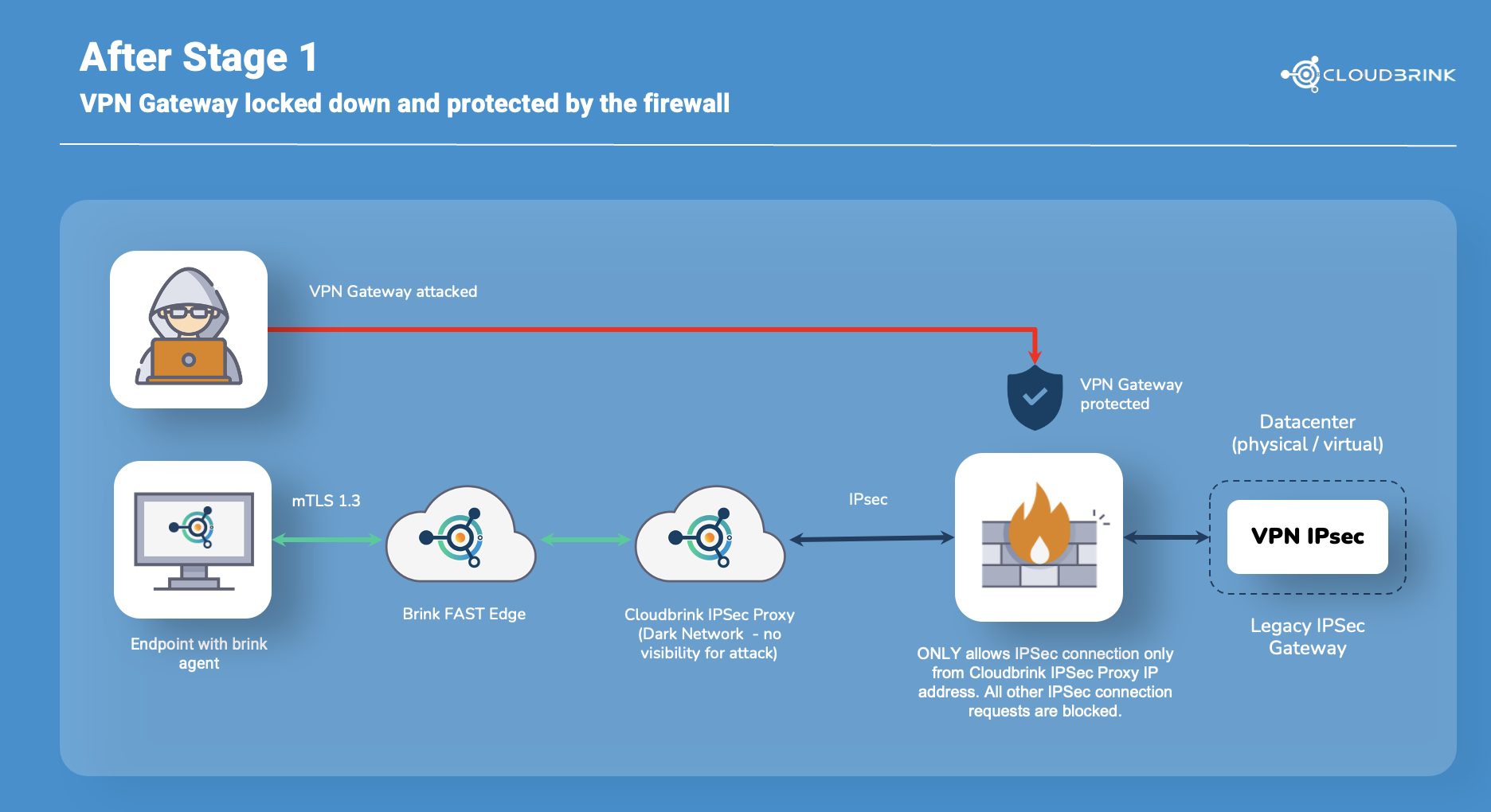
The diagram above shows Cloudbrink’s approach to securing IPSec VPN gateways. Adding Cloudbrink addresses critical vulnerabilities that have long plagued traditional remote access solutions. Legacy IPSec VPN gateways are inherently exposed, requiring open ports to accept incoming connections from any potential client. This exposure creates a broad attack surface, allowing cybercriminals to probe for weaknesses, exploit zero-day vulnerabilities, and gain unauthorized access to the data center. Once attackers infiltrate the VPN gateway, they can move laterally, compromise sensitive systems, and exfiltrate data.
By integrating Brink FAST and the Brink IPSec Proxy, Cloudbrink eliminates these risks by fundamentally changing how organizations manage IPSec connections. Instead of an open gateway susceptible to attack, the VPN now only accepts connections from a tightly controlled Brink IPSec Proxy. Any unauthorized connection attempts are automatically blocked, reducing the attack surface significantly.
Additionally, users must authenticate through BrinkAgent before accessing the VPN, meaning System Admins can restrict access to verified, authorized, and compliant devices. This model prevents attackers from even seeing the VPN gateway, let alone attempting to breach it. Cloudbrink’s approach not only fortifies security but also simplifies access control, making remote connectivity both safer and more resilient against evolving threats.
Cloudbrink: A Next-Generation Approach to Secure Remote Access
The Cloudbrink approach to network connectivity and security uses a modern Zero Trust Network and Secure Access Service Edge combination. The key aspects of the Cloudbrink approach that make it both an ideal remote access solution in its own right and suitable to plug the security gaps commonly discovered in Fortinet (and other legacy VPN) solutions include:
Dark Network Implementation: Eliminating Attack Surfaces
Unlike Fortinet VPNs, which need open inbound network ports, no ports get exposed to the public internet in Cloudbrink’s design. Cloudbrink uses a fully outbound-only dark network connectivity model, making it invisible to threat actors and preventing direct attacks. Its architecture is based on a zero-trust framework, requiring continuous authentication and authorization.
Automated Moving Target Defense (AMTD): Dynamic Security at Scale
Traditional VPNs use static encryption keys and fixed IP addresses, which makes them susceptible to long-term, persistent attacks. In contrast, Cloudbrink uses AMTD to rotate security certificates several times per day, effectively countering low-and-slow cyberattacks that depend on prolonged access.
High-Performance ZTNA with Adaptive Routing
Cloudbrink builds on Zero Trust Network Access (ZTNA), which dynamically enforces access controls for each session. Its adaptive routing algorithms automatically identify the fastest and most secure network paths, reducing latency and enhancing connectivity performance speeds up to 30x (Ref 3). Unlike Fortinet’s VPNs, which can experience packet loss and congestion, Cloudbrink ensures seamless connectivity through intelligent packet loss recovery mechanisms. This means that if you migrate to a Cloudbrink native remote access solution, you’ll improve both security and performance for your remote workforce.
Last-Mile Optimization with FAST Edge Technology
Traditional VPNs route traffic through centralized data centers, which can create performance bottlenecks. In contrast, Cloudbrink’s distributed FAST Edge network uses thousands of globally distributed Points of Presence (PoPs) to minimize latency and improve reliability. As a result, remote users can enjoy performance that feels like being in the office, no matter where they work.
No Patch Dependency: Built-in Resilience Against Zero-Day Exploits
Fortinet’s ongoing security vulnerabilities force businesses into a continuous cycle of patching. Cloudbrink’s zero-trust encrypted tunnels prevent typical remote code execution, authentication bypass, and credential harvesting attacks by design. With Cloudbrink, enterprises no longer need emergency patches in these situations to avert catastrophic breaches.
Getting the full benefits of Cloudbrink
Transitioning fully to Cloudbrink unlocks enhanced security, improved performance, and streamlined operations and management. This process involves replacing the VPN gateway with a Cloudbrink connector, ensuring a smoother, more efficient migration.
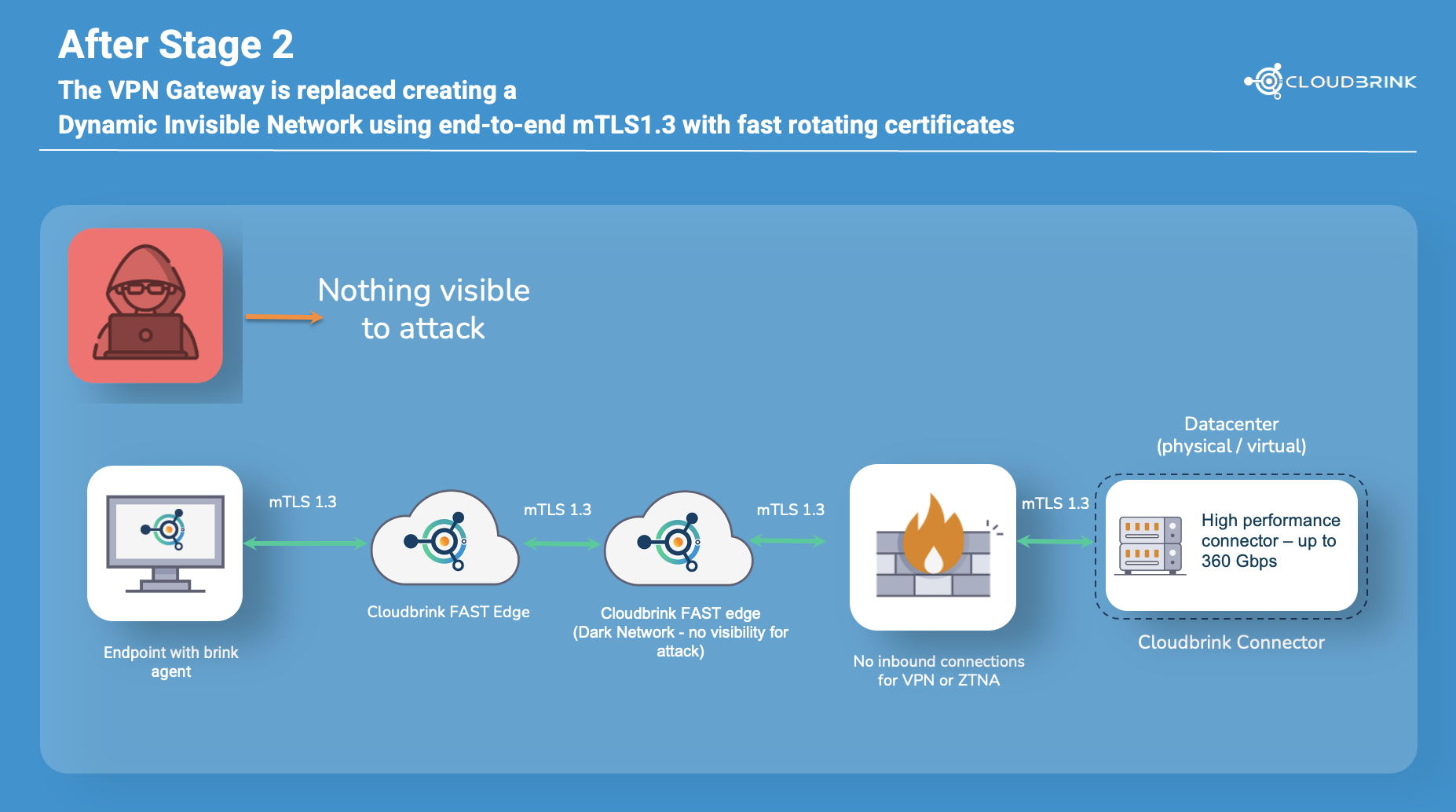
Conclusion
The recurring vulnerabilities in Fortinet’s VPN solutions highlight the urgent need for businesses to deploy access solutions that don’t need System Admins frequently applying patches to keep them secure. By adopting Cloudbrink, you can eliminate the constantly emerging vulnerabilities in Fortinet VPNs and secure networks against zero-day threats using a proactive, zero-trust solution. Plus, you can fully migrate to Cloudbrink over time for even better performance and easier remote access management for your IT teams.
Find Out More
Take control of your network security and eliminate the risks of zero-day vulnerabilities for good. Deploy Cloudbrink’s Personal SASE solution and empower your workforce with the security, speed, and simplicity they deserve.
For a demo and to learn more about how Cloudbrink can transform your organization’s VPN, visit our Request a Demo page.
References
- Fortinet CVEs – https://www.cve.org/CVERecord/SearchResults?query=Fortinet
- CVE-2024-55591 – https://nvd.nist.gov/vuln/detail/CVE-2024-55591
- Broadband Performance Tests of the Cloudbrink Service – https://cloudbrink.com/broadband-performance-tests-summary/