Cyber threats are evolving rapidly, with more sophisticated attacks emerging on a daily basis. A single weak link in the security chain can compromise the entire digital ecosystem, which is where Zero Trust Network Architecture (ZTNA) comes into play. ZTNA assumes that no implicit trust exists within the network, and every request must be secured and authorized. One of the most important ways of accomplishing this is via using the Transport Layer Security (TLS) protocol to secure the end-to-end communication path.
However, not all TLS protocols are created equal, and usage of outdated or weak TLS protocols can result in significantly weakened security that can threaten the entire network. It can also result in a false sense of security, with customers not realizing that the security mechanisms they place trust in, can be easily compromised by threat actors.
Is TLS 1.2 still secure?
The TLS protocol has evolved over the years, improving with each iteration, with TLS 1.2 being a significant step forward over previous versions. It improved over its predecessor’s hashing techniques and enhanced its authentication and encryption capabilities.
However, as attacks have become more and more sophisticated, TLS 1.2 is now also outdated, containing several vulnerabilities that attackers can easily exploit.
Some of the critical areas of concern in TLS 1.2 are:
- Usage of insecure cipher suites such as the RC4 key exchange algorithm, the RC4 stream cipher, and the CBC mode cipher that attackers can easily exploit.
- Vulnerability to attacks such as BEAST and POODLE that can be exploited for data theft.
TLS 1.3 has been released to address these flaws, yet despite using modern encryption algorithms with better performance, adoption of the new TLS version has been slow among vendors due to several reasons:
- TLS 1.3 is ubiquitous within most network architectures and applications. Security product vendors know this and want to avoid the massive effort required to phase out TLS 1.2 completely within their networks, such as testing, re-certifications, etc.
- Vendors with a Datacenter Point of Presence (PoP) have hardware-based appliances that rely on TLS 1.2. These must be physically replaced, which can take considerable time and money to carry out.
Security Vendors often attempt workarounds around this by either downplaying the inherent weaknesses present with TLS 1.2 or implementing TLS 1.3 partially for front-end facing interfaces. This leaves an insecure backend infrastructure running on vulnerable and legacy protocols that can be exploited by the attacks we mentioned earlier.
This results in a flawed ZTNA being implemented, which is insecure from the onset, and companies not realizing the benefits of Zero Trust. This practice of leaving the back end insecure is equivalent to implementing a state-of-the-art lock on the front door and yet leaving the back door wide open!
Enter TLS 1.3
CloudBrink, a next generation Zero Trust product realizes the benefits of adopting a solid security foundation in its core and has implemented TLS 1.3 in every link of its communication chain. This product takes full advantage of the benefits that TLS 1.3 provides such as superior security, performance, and resilience to cyberattacks.
Customers can have full confidence that they are future-proofing their network against cyber threats that exploit TLS 1.2 vulnerabilities, unlike other Zero Trust products.
How CloudBrink leverages TLS 1.3
CloudBrink’s adoption of TLS 1.3 is not just surface level but consistently applied across its architecture and communication reinforcing the company’s commitment to a true zero-trust approach.
Some of its key differentiators are:
- Usage of a High-Performance Zero Trust Network Access (ZTNA) service that employs mutual TLS 1.3 to provide a robust and mature zero trust model.
- A unique feature called the Moving Target Defense (MTD) rotates security certificates hourly instead of in months or years. The result is a significantly enhanced level of security and a reduced attack surface. Attackers have a much shorter window to exploit a given security certificate before it changes.
- Every component in the Cloudbrink architecture is provisioned with dynamic PKI certificates for trusted TLS communication that cannot be intercepted. These PKI certificates are automatically refreshed at frequent intervals to maintain the security posture. These features are entirely transparent to the customer as they are part of the solution itself instead of an add-on that must be paid separately. Customers are entirely relieved from the overhead of managing a PKI infrastructure.
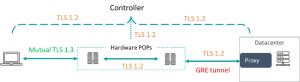
The following diagram illustrates how Cloudbrink uses the latest TLS 1.3 cipher within every touchpoint. This combination of Mutual TLS and TLS 1.3 at each and every segment in the end-to-end path ensures that customers gain the highest level of security posture while cyber risks are minimized significantly.
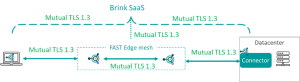
By the way – using mutual TLS 1.3 combined with FAST edges instead of traditional weak PoPs makes the Cloudbrink solution deliver up to 30 times the application performance when compared to other VPN, ZTNA, and SDP solutions like Palo Alto, Zscaler, and Permiter 81.
Conclusion
ZTNA as a security concept can be achieved only when the solution adopts security into its very DNA and not as an add-on. Customers must look past the shiny veneer of other security products that may profess to use TLS 1.3 while still relying on outdated and vulnerable protocols within their backend infrastructure.
CloudBrink’s consistent usage of TLS 1.3 demonstrates its commitment to achieving an accurate ZTNA model while providing a significant advantage over competitors. The old saying that security is only as strong as its weakest link is as applicable today as it was decades ago. Customers must ensure that the solution they choose embodies this phrase and implements Zero Trust as a concept, not a marketing gimmick.