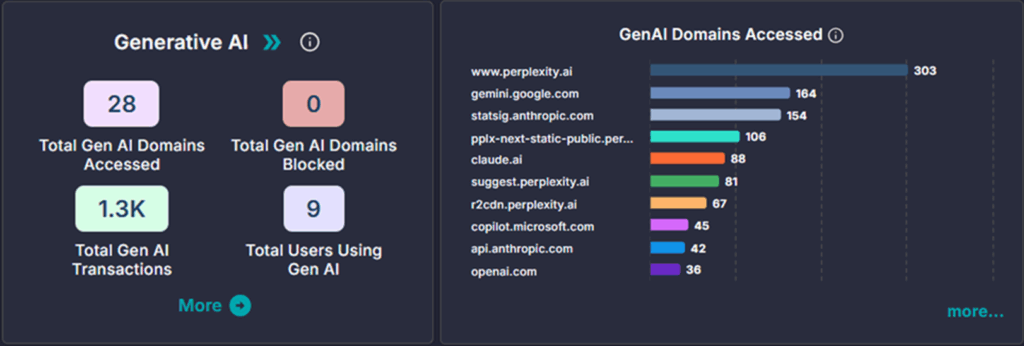
Did you know that 83% of enterprise traffic now bypasses traditional network perimeters? This shift has rendered castle-and-moat security models obsolete, forcing organizations to rethink how they protect their digital assets. As remote work becomes permanent and cloud adoption accelerates, three security frameworks have emerged as frontrunners: ZTNA, SASE, and CASB.
What Makes These Security Models Different?
Think of your organization’s security needs like protecting a modern city. Traditional firewalls are like ancient city walls—they worked when everyone lived inside the walls, but now your citizens (employees) live everywhere, work from coffee shops, and need access to services scattered across different neighborhoods (cloud applications).
Zero Trust Network Access (ZTNA) acts like a sophisticated ID verification system. Every person must prove their identity and authorization for each building they want to enter, regardless of whether they’re coming from inside or outside the city.
Secure Access Service Edge (SASE) is like having a comprehensive city management system that combines transportation, security, and utilities into one coordinated service. It merges networking and security functions into a single cloud-delivered platform.
Cloud Access Security Broker (CASB) functions as a specialized security checkpoint specifically for cloud services—imagine a customs office that inspects everything flowing between your organization and external cloud providers.
Zero Trust Network Access: The “Never Trust, Always Verify” Approach
ZTNA operates on a fundamental principle: trust no one, verify everyone. When your employee tries to access a company application, ZTNA doesn’t care if they’re sitting in the corporate office or working from a beach in Bali.
How ZTNA Should Work in Practice:
- Authenticates users based on multiple factors (device health, location, behavior patterns)
- Grants access to specific applications, not entire networks
- Continuously monitors sessions for suspicious activity
- Terminates access immediately when risk levels change
Your organization benefits most from ZTNA when you have:
- Remote workers accessing sensitive applications
- Third-party contractors needing limited system access
- Compliance requirements demanding strict access controls
- Legacy applications that need modern security without infrastructure overhaul
Real-world example: A healthcare company uses ZTNA to let doctors access patient records from their personal devices while ensuring HIPAA compliance. The system verifies the doctor’s identity, checks device security status, and grants access only to specific patient files needed for current cases.
SASE: The All-in-One Security and Networking Platform
SASE represents a architectural shift—instead of buying separate tools for networking and security, you get everything from one cloud-based provider. It’s like switching from managing multiple utility companies to having one provider handle electricity, water, internet, and security monitoring.
Core SASE Components:
- SD-WAN for intelligent traffic routing
- Cloud firewall for network protection
- ZTNA for application access
- CASB for cloud security
- Data loss prevention and threat protection
SASE makes sense for your organization when:
- You’re tired of managing multiple point solutions
- Network performance issues affect productivity
- IT teams spend too much time integrating different security tools
- You want predictable, consolidated billing for security and networking
Consider this scenario: A retail chain with 200 locations previously managed separate contracts for internet connectivity, firewalls, VPN solutions, and cloud security. SASE consolidated everything into one platform, reducing complexity while improving performance for point-of-sale systems and inventory management.
CASB: Your Cloud Application Security Specialist
While ZTNA and SASE address broad security architectures, CASB focuses specifically on protecting your cloud application usage. Think of CASB as a specialized translator that sits between your organization and cloud services, ensuring conversations follow security protocols.
What CASB Monitors and Controls:
- User activity across cloud applications (who’s accessing what, when, and how)
- Data movement to prevent sensitive information from leaving approved channels
- Application permissions to ensure employees don’t accidentally grant excessive access
- Compliance violations before they become regulatory problems
Your organization needs CASB when:
- Employees use multiple cloud applications for daily work
- Sensitive data regularly moves through cloud services
- Compliance regulations govern your cloud usage
- Shadow IT creates security blind spots
Practical application: A law firm uses CASB to monitor how attorneys share documents through cloud storage services. The system automatically encrypts confidential client files, prevents sharing with unauthorized email domains, and generates audit reports for compliance reviews.
Making the Right Choice for Your Organization
The decision isn’t always either-or. Many organizations combine these approaches based on specific security challenges and business requirements.
Start with ZTNA if:
- Remote access security is your primary concern
- You need granular application-level control
- Budget constraints require focused investment
- Legacy systems need modern access controls
Choose SASE when:
- Network and security management complexity overwhelms your team
- Multiple locations need consistent security policies
- You prefer comprehensive solutions over point products
Implement CASB if:
- Cloud applications handle most of your business processes
- Data protection regulations apply to your industry
- Employees frequently share files through cloud services
- You need visibility into cloud application usage patterns
Key Considerations for Implementation
Budget Impact: ZTNA typically requires the smallest initial investment, while SASE represents the largest commitment. CASB costs vary significantly based on the number of cloud applications and data volume you need to monitor.
Timeline Expectations: ZTNA deployments often complete within weeks for specific applications. SASE implementations can take months due to network architecture changes. CASB deployments fall somewhere in between, depending on cloud application complexity.
Staff Requirements: Each approach demands different expertise. ZTNA requires identity and access management skills. SASE needs network engineering knowledge. CASB demands cloud security and compliance expertise.
Your security infrastructure should adapt as your business evolves. What works today might need adjustment as you adopt new applications, expand to different locations, or face changing compliance requirements. The most successful organizations regularly assess whether their chosen approach still matches their security needs and business objectives.