As the demand for remote work solutions continues to grow, so does the need for robust, secure, and efficient secure remote access services. Hybrid workforce and the solutions that enable hybrid work have become prime target for attackers because of the increased attack surface.
Pulse Secure VPN
Ivanti’s VPN, Connect Secure, formerly known as Pulse Secure, is one such platform that has been widely adopted. However, recent vulnerabilities identified in the system have raised concerns about its security and reliability 1.
The Latest Vulnerabilities: CVE-2023-46805 and CVE-2024-21887
In early 2024, two significant vulnerabilities were reported in Ivanti Connect Secure: CVE-2023-46805 and CVE-2024-21887 2 3. These vulnerabilities impact all supported versions of the products 1.
CVE-2023-46805 is an authentication bypass vulnerability found in the web component of Ivanti Connect Secure. This issue allows an attacker to gain unauthorized access to the system 4.
On the other hand, CVE-2024-21887 is a command injection vulnerability in the web components of Ivanti Connect Secure and Ivanti Policy Secure. This allows an authenticated attacker to execute arbitrary commands 5.
There have been several reports that indicated that these vulnerabilities have been exploited by the attackers already at hundreds of customer deployments for more than 8 months [1].
User Dissatisfaction with Ivanti Connect Secure
While these vulnerabilities are a primary concern, some users have expressed dissatisfaction with Ivanti Connect Secure for various reasons.
- Limited Customer Support: Users have reported slow response times and limited assistance from the customer support team, leading to delays in resolving issues.
- Performance Issues: There have been instances of performance issues, including slow connection times and frequent disconnections. This can disrupt productivity and lead to user frustration.
- No SaaS protection: Ivanti Connect Secure still follows the old legacy appliance model where user traffic must go through the appliance for any security. With SaaS and Cloud-based apps being adopted significantly, appliance-based solutions have lost relevance in the new hybrid IT deployment scenarios.
- Lack of Transparency: The recent vulnerabilities have highlighted a perceived lack of transparency from Ivanti. Users expect regular updates regarding potential security threats and steps taken to mitigate them.
Moving Forward
In response to the latest CVEs, Ivanti has released security updates to address these vulnerabilities 6. These are still workarounds only and the final patch for security issues is expected later in 2024 [2]. It is crucial for businesses using Ivanti Connect Secure to apply these workarounds promptly to mitigate potential risks or move off the platform.
One platform that major Ivanti customers have moved to is the Cloudbrink high-performance ZTNA. After testing around 20 VPN, SDP, and ZTNA solutions, a Fortune 100 company found that Cloudbrink outperformed other secure remote access solutions by up to 30x. Some of the results can be seen below.
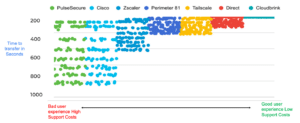
A review of Ivanti Connect Secure shows it has security weaknesses and terrible performance issues while the Cloudbrink service with its automated moving target defense (AMTD) reduces the attack surface and accelerates the users’ network and application performance.
Why Cloudbrink?
- Hardened security: Cloudbrink has used only highly recommended security practices such as TLS 1.3 protocols, mutual TLS connections at every segment, rotating certificates every few hours, Dark Cloud security for SaaS and private apps, SDP-compliant datacenter deployments, and complete Zero-Trust capabilities.
- Superior performance: Cloudbrink stack has been built ground-up from the start with performance as well as security in mind. So, customers need not trade-off between performance vs security.
- Flexible and easy deployments: Customers can roll out Cloudbrink in few minutes because it is a completely software-only solution. There is no shipment of appliances or application or network changes that customers have to make.
- Agile scalability: Since Cloudbrink is completely as-a-service model, customers can scale from a few 10s of users to 1000s of users at their own pace. There is no need for upfront commitment or capex that customers have to incur to start migrating to Cloudbrink.
- Future-ready: At the corporate executive level, all enterprises globally are evaluating solutions that will support their business for the next decade. Zero-trust solutions provide the required security and hybrid work solutions that customers are looking for. Cloudbrink has been consistently winning customers with superior security and performance benefits.
Conclusion:
With users seeking to work from anywhere and IT teams deploying apps where they are most efficiently run, including multi-cloud deployments, enterprises are struggling to find the perfect balance between security, performance, and simplicity of management of all these entities. The only way to navigate in such a complex solution is to make the right choice for each solution and let the leading solution provide best outcomes for the enterprise.
It is important for enterprises to evaluate multiple options and select the most effective solution for a remote workforce and not get into the traps of consolidated platforms or lowest lowest-priced solutions or product bundles that provide only “me-too” products. The cost of a security incident is so significantly high that any form of trade-off is not justified.
Footnotes
- https://www.ivanti.com/blog/security-update-for-ivanti-connect-secure-and-ivanti-policy-secure-gateways 2
- https://www.volexity.com/blog/2024/01/18/ivanti-connect-secure-vpn-exploitation-new-observations/
- https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US
- https://www.cisa.gov/news-events/directives/ed-24-01-mitigate-ivanti-connect-secure-and-ivanti-policy-secure-vulnerabilities
- https://www.cvedetails.com/vulnerability-list/vendor_id-17398/Ivanti.html
- https://www.cisa.gov/news-events/alerts/2024/01/10/ivanti-releases-security-update-connect-secure-and-policy-secure-gateways
- https://forums.ivanti.com/s/article/CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US
[1] https://www.darkreading.com/vulnerabilities-threats/third-ivanti-vulnerability-exploited-in-the-wild-cisa-reports
https://forums.ivanti.com/s/article/CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US