 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
An old security technology that has gotten little attention is finally ready for a new closeup.
It goes by the name polymorphic code — or alternatively, automated moving target defense or AMTD — and it has been around for nearly a decade. It came into its own around 2017 when was popularized by both malware writers and defenders.
And once again, security professionals are playing another cat-and-mouse game, but this time the stakes are a lot higher thanks to better tools on both sides.
On the malware side, the term describes code that can adapt to conditions and change its behavior to try to avoid detection. It cuts across a wide swath of computing circumstances, including the ability to attack runtime memory, file systems, credentials, virtual machines, workloads, containers and network connections.
An example is the After-Shock-3PC malware that targeted a number of media websites. It frequently switched its active code to spoof online payment systems, in the process trying to appear as if it belonged on the computers that it infected. It was even partially successful.
But what is good for the malware goose is also good for defensive security ganders. For example, Morphisec Ltd. is focusing exclusively on polymorphic defensive methods to protect against the evolving threats. Think of its approach as a better mousetrap, so that a potential attacker will have trouble entering a network and finding a vulnerable endpoint.
The company has been in business for eight years, raising $50 million in several funding rounds and protecting 5,000 organizations and 9 million endpoints. Its defenses combine several methods, including:
Other security providers claim to incorporate polymorphic methods as well, mostly as one of several tools used for better malware detection. These include products for endpoint protection,such as Malwarebyte Inc.’s Anti-Exploit feature, zero-trust network access such as Cloudbrink Inc., web app protection, email security gateways and intrusion detection products such as Zscaler Inc.’s Data Protection.
There have been several acquisitions of note as well: In 2019, F5 Networks Inc. bought Shape Security in 2020 and has incorporated Shape’s technology into its Distributed Cloud Bot Defense. Two early polymorphic defenders have moved on: CyActive disappeared when it was purchased by PayPal, although this merger could be considered a testimonial for the importance of polymorphic defenses in e-commerce. Another early player was Polyverse, which still claims to use the technology, but its has refocused its efforts on other cybersecurity offerings.
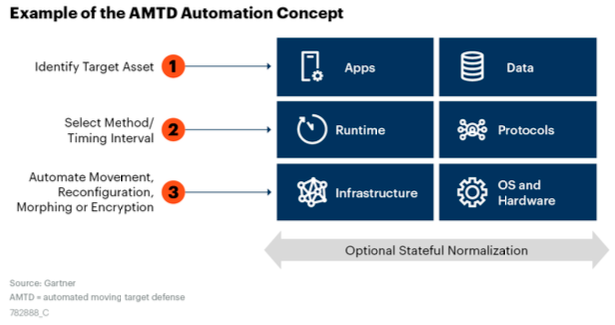
Earlier this year, Gartner Inc.’s Lawrence Pingree wrote an analysis of polymorphism. Pingree said it’s “an emerging game-changing technology … and significantly can enhance the effectiveness and value of other security solutions.”
Gartner recommends pairing polymorphism with various automated detection techniques and predicts that within two years, a quarter of all cloud apps will have these technologies built in. “This technique can be effective at thwarting the execution of common software vulnerabilities and exposures.” The report describes an interesting future ahead for defensive technology and the ways in which pervasive polymorphism can become across numerous security products in the coming years.
The first piece of polymorphic malware can be traced to 1990 with Ralf Burger’s Chameleon. By 2019, Webroot’s annual threat assessment reported that almost all malware it has seen had demonstrated polymorphic properties.
It became popular because criminals can purchase malware construction kits that include this feature, such as the kits that have produced the Cobalt Strike, Fallout and Orcus malware families. Indeed, it could be argued that it’s so frequently found in malware that most attack descriptions don’t even call it out specifically.
 Polymorphic malware scrambles its actions, such as using different memory structures, making the malware harder to locate by threat hunters (pictured, adjacent). “Cybercriminals arm their malware with polymorphism, obfuscation, encryption and self-modification to evade detection and maintain unpredictability,” product marketing director Oren Dvoskin wrote on Morphisec’s blog last year. These tactics give attackers an advantage over legacy security technology’s reliance on static analysis, signatures, file reputation and anomaly detection methods.
Polymorphic malware scrambles its actions, such as using different memory structures, making the malware harder to locate by threat hunters (pictured, adjacent). “Cybercriminals arm their malware with polymorphism, obfuscation, encryption and self-modification to evade detection and maintain unpredictability,” product marketing director Oren Dvoskin wrote on Morphisec’s blog last year. These tactics give attackers an advantage over legacy security technology’s reliance on static analysis, signatures, file reputation and anomaly detection methods.
The attackers have a further advantage, thanks to artificial intelligence. New research from GitGuardian has uncovered how “ChatGPT can be prompted to generate dynamic, mutating versions of malicious code at each call, making the resulting vulnerability exploits difficult to detect by cybersecurity tools,” CSOonline wrote in covering the story. The researchers put together a proof-of-concept demonstrating the premise.
Dvoskin told SiliconANGLE that Morphisec’s software “creates a dynamic and unpredictable attack surface that is challenging to target, so it doesn’t need to rely on AI tools for core protection.” In the meantime, malware authors will continue to incorporate AI-based methods into new strains, making them even harder to detect.
THANK YOU